
The Human Firewall: Your First Line of Defence
We have always advocated that when it comes to cybersecurity, the first line of defence is user common sense. This "human firewall" can be strengthened through consistent staff training, awareness programs, and by elevating the profile of cybersecurity risks across your business.
According to a report by Howden Insurance Group, UK businesses have lost over £44bn in the last five years to cyber attacks. Today, we're sharing a real-world example that landed in our inbox—one that demonstrates why technical controls alone aren't enough.
The Incident: A Masterfully Crafted Scam
Our accounts department received an email earlier today chasing a payment. The email contained a chain of email history, including one email that appeared to show our CEO previously approving the payment. The email was very well written and looked very convincing, see below…
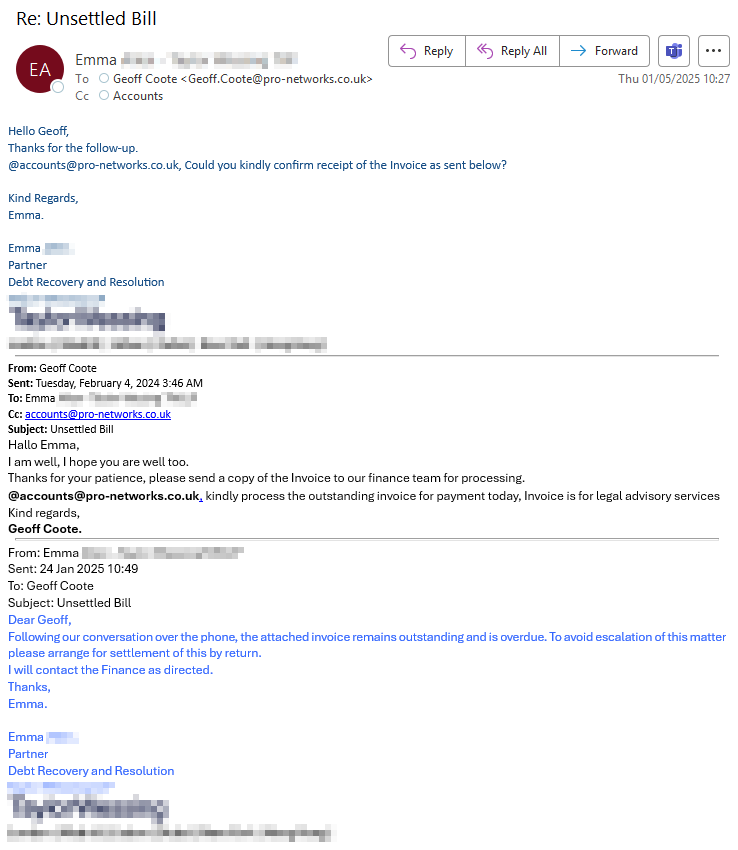
Red Flags Hidden in Plain Sight
At first glance, the email appears legitimate. It shows that Geoff (our CEO) has approved payment in the second email (dated February 4th) in the chain, and "Emma" had requested this in the original email (dated January 24th).
However, closer inspection reveals several concerning red flags:
- Timeline inconsistency: The reply email is dated February 4, 2024, while the original email is from January 24, 2025—an impossible chronology
- Missing specifics: No invoice amount, reference number, or service details are provided
- Pressure tactics: Note the language about "overdue" invoices and threats of "escalation"
- False authority: The fabricated email from Geoff copying our accounts department was designed to add legitimacy to the request
- Professional impersonation: "Emma" presents herself as a "Partner, Debt Recovery and Resolution" to create urgency and fear
Technical Analysis: Why This Bypassed Security Controls
The particularly clever part of this scam is that the emails dated January 24th and February 4th never actually happened—they were never sent or received, but were fabricated to appear as a legitimate thread.
The sender's display name at the top of the email was crafted to look authentic, a common tactic scammers use. The actual email address was created in Microsoft 365, using a non-existent domain name similar to the organisation they claimed to represent, helping it avoid appearing on known deny lists.
This "clean" domain, combined with well-structured content meant the email easily passed standard anti-spam measures. Additionally, since the email wasn't:
- Asking for credentials via a spoofed site
- Containing malicious file attachments
- Including suspicious links
...managed SOC services like MDR and ITDR would not detect or prevent this fraud attempt.
How We Caught It: Our Two-Pronged Defence
The reasons this attempted fraud was denied were twofold:
- Staff Awareness – We invest in monthly security training and testing for our team to ensure they remain vigilant about the latest scams. This continuous education has significantly increased awareness and detection capabilities.
- Payment Verification Protocols – We maintain a strict policy that all payment requests received via email must be verbally confirmed with the supposed sender before any transaction is processed. This simple but effective step has prevented numerous fraud attempts.
Protecting Your Business: Action Steps
Based on our experience, we recommend implementing these measures immediately:
- Implement the "Two-Person Rule" for all payment changes and financial requests
- Establish verification protocols that require out-of-band confirmation (phone call to a known number, not one provided in the email)
- Create a payment request form with required fields that help identify suspicious requests
- Conduct regular phishing simulations specific to financial fraud scenarios
- Review email configurations to clearly mark external emails
The Bottom Line
Even as security technologies continue to advance, social engineering tactics evolve in parallel. Building a culture of security awareness remains your most effective defence against increasingly sophisticated scams.
Have you encountered similar scam attempts in your organisation? Contact us today for a comprehensive security assessment to identify potential vulnerabilities in your human and technical defences.
